Quick Triage - Obsidian Malware Campaign

Intake
In July 2024, a user on the subreddit for the note-taking application Obsidian made a post warning users of a malicious site masquerading as Obsidian's homepage, obsidian.md.
The malicious website (obsidianworking[.]com) was shut down almost immediately after the initial reddit post was made, but some archives exist, which will provide an opportunity to quickly triage this site. I am only interested in some quick pivots, and determining if this is a phishing scam or infostealer dropper.
Triage Notes
Malicious URL: obsidianworking[.]com/main.php
The site is unavailable, but an archive is available at URLscan.io.
A quick glance at the DOM shows the malicious site is basically a carbon copy of the legitimate Obsidian site, but some extra javascript pasted in. The js is lightly obfuscated, and we can surmise the endpoints contacted by the script are likely downloading something malicious. Looking at the site in VirusTotal, we can see that the website downloads a file called "obsidian.exe"
While google dorking the domain, I came across this article by hyde at solothreats, which gives a detailed run-down of the infection chain. Hyde was able to analyze the malicious domain when it was still online, and documented it dropping likely infostealers targeting PC and Mac operating systems.
This is the extent of the triage, but one thing I want to point out is the two malware samples targeting Windows are each signed with a compromised certificate. These signers stood out like a sore thumb. Here they are for each of the Windows samples.
b4346702b4b5029cbd627b5df724550f8b783ba22876e5070dadc0ed5c214df2
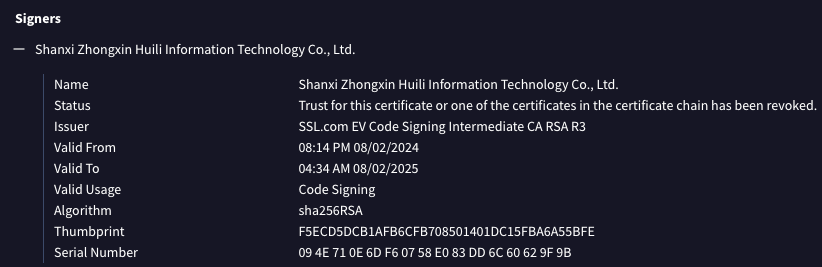
1662a66e1a343e91964017b085ce85f4167b802f3f7c47e4e9c8b2e9a52e77b1
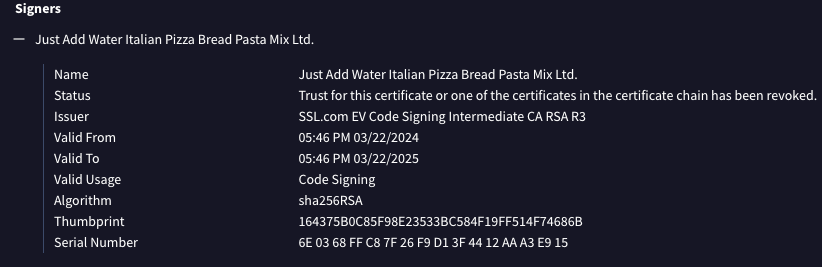
Thankfully, they have already been revoked explicitly by the CA, so no need to further report. But if they were still up, I would have used the certReport utility by Squiblydoo.
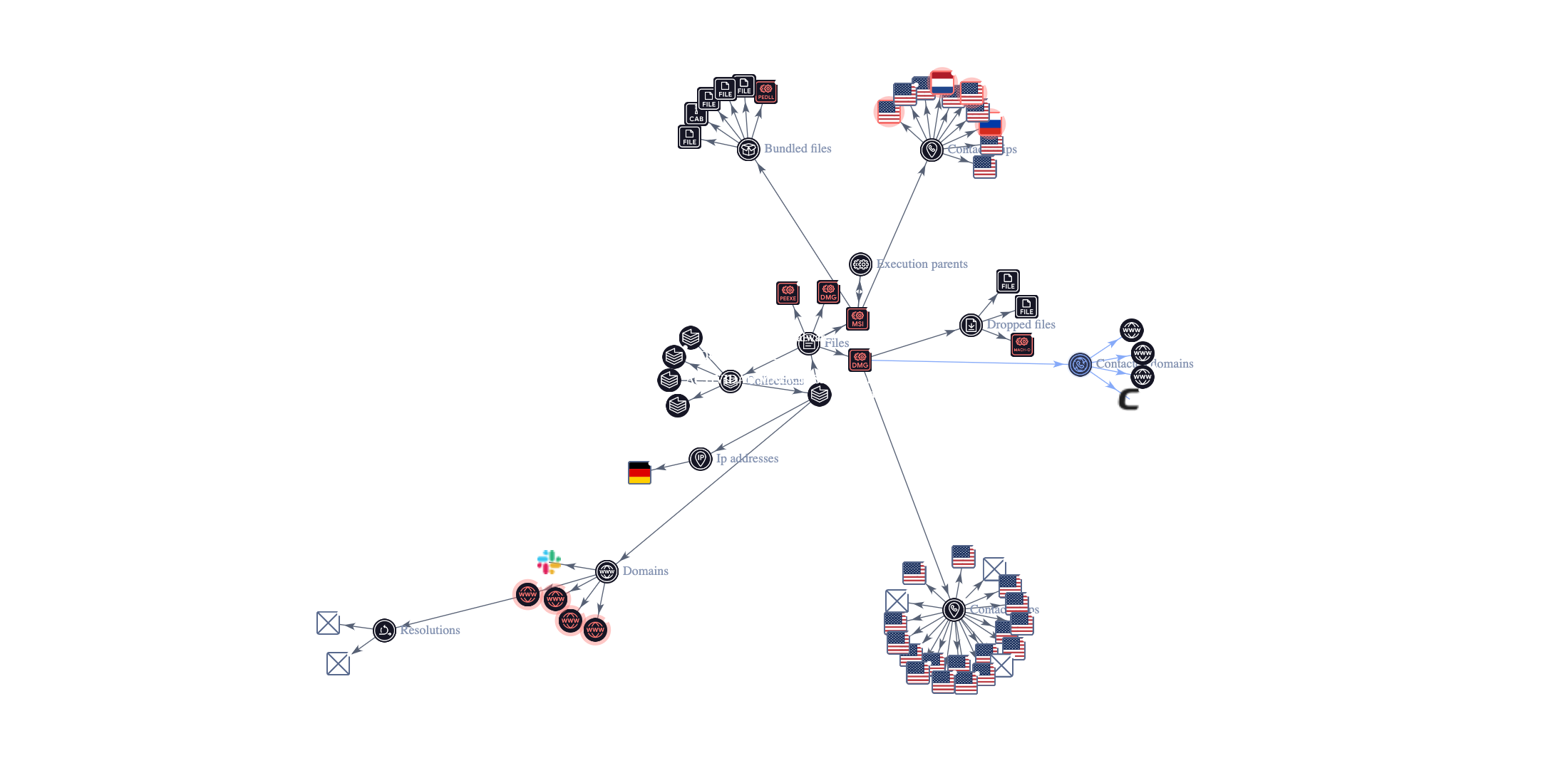
Virustotal Graph
With just one pivot in VT graphs, some of our IOCs overlap with Rhadamanthys IOCs.
IOCs
IOCs are available to download at the following locations:
Network
| Type | Value | Comment |
|---|---|---|
| domain | obsidianworking.com | original domain which triggered the investigation. It is masquerading as the legitimate obsidian domain (obsidian.md). Further analysis indicates it drops windows or mac malware. |
| domain | gztxbb.com | [solothreats] Downloads Mac malware. Hyde noted that the code on this site was continuously updated during the observation period. |
| domain | dropsforbox.com | [solothreats] Downloads Windows malware |
| domain | adminnnnnxxxxx123.com | [solothreats] Likely tracker for clicks on phishing domain. |
| domain | adminforbusiness.com | [solothreats] Likely tracker for clicks on phishing domain. |
| ipv4 | 46.4.13.241 | [solothreats] IP which the gztxbb[.]com domain was resolving to at the time of Hyde's artcile. |
File
| Type | Value | Comment |
|---|---|---|
| sha256 | 1662a66e1a343e91964017b085ce85f4167b802f3f7c47e4e9c8b2e9a52e77b1 | [solothreats] filename: obsidian.exe. Windows malware masquerading as the notetaking app Obsidian. |
| sha256 | b4346702b4b5029cbd627b5df724550f8b783ba22876e5070dadc0ed5c214df2 | [solothreats] filename: Obsidian_Installer_v.3.15.exe. Windows malware masquerading as the notetaking app Obsidian. |
| sha256 | 2d52d65e91ead764be7e9c4e1bb5e97d4becbcb0f2314c445c18a6bb24b91de4 | [solothreats] filename: Obsidian_v.1.7.malware.dmg. Mac malware masquerading as Obsidian. Possibly AMOS steler. |
| sha256 | 46ed397a3907971ffdf3111ec78c23022e5f6037b409404af30acd5865a02670 | [solothreats] Filename: Obsidian_v.2.10.dmg. Mac malware masquerading as Obsidian. Possibly AMOS stealer. |
